The Blockchain Community needed Ethereum to win!
The bitcoin protocol saw the first adoption of blockchain, but it had many limitations. Ethereum aimed to correct those limitations. Let's see how!
Table of contents
- Introduction
- What is a blockchain?
- A practical guide to understanding Blockchain
- A simple implementation of the blockchain technology using python:
- Bitcoin protocols were limited
- Why Ethereum was so important for the Blockchain Community
- Components of the Ethereum Blockchain:
- Problems with Ethereum being Turing Complete
- Bitcoin fixes this...
- Conclusion
- References for further reading
Introduction
The bitcoin white paper was released over 13 years ago. Although the idea has come a long way since then and has received some mainstream adoption, the idea still feels fringe. The theory proposed by the bitcoin white paper author, of the pseudonym Satoshi Nakamoto, was set to disrupt financial institutions by redefining the way they see assets and how those assets are stored and used by outsourcing the creation and distribution of these assets from the government and financial institutions -with a single point of failure- to a decentralised, trustless database where individuals can make censorship-resistant moves and store their assets in a blockchain.
What is a blockchain?
Blockchain makes the digital asset, bitcoin, that Satoshi Nakamoto proposed in the white paper truly decentralised. The blockchain acts as a public ledger that stores information digitally and is maintained by nodes(a single instance of a decentralised network that stores, shares, and preserves data on the block) accessible to everyone. The amount of digital assets (bitcoin) you have is based on your transaction history on the blockchain. If this seems like a lot(I know it was for me🥲), let's walk through a practical use case of how public ledgers work using cryptography and how they become more decentralised with time when the parties participating in the system begin to trust each other less.
A practical guide to understanding Blockchain
Charles, Angie, Christina, and Andrew are university housemates. They often pay for things together, from electricity bills to dinner bills. Each time the need for payment arises, they have to split the bill in four ways which became cumbersome after a while, so because of that, Angie created a ledger where they record all payments that were made by each other, and they will all pay up what they owe at the end of the month. This system reduces the need for them to split the bill for everything immediately. For instance, if Christina makes a payment of 100 dollars for cable TV, she goes to write it on the ledger that Charles, Angie, and Andrew each owe her 25 dollars, and at the end of the month, they would make that payment. Pretty Simple(This is me foreshadowing).
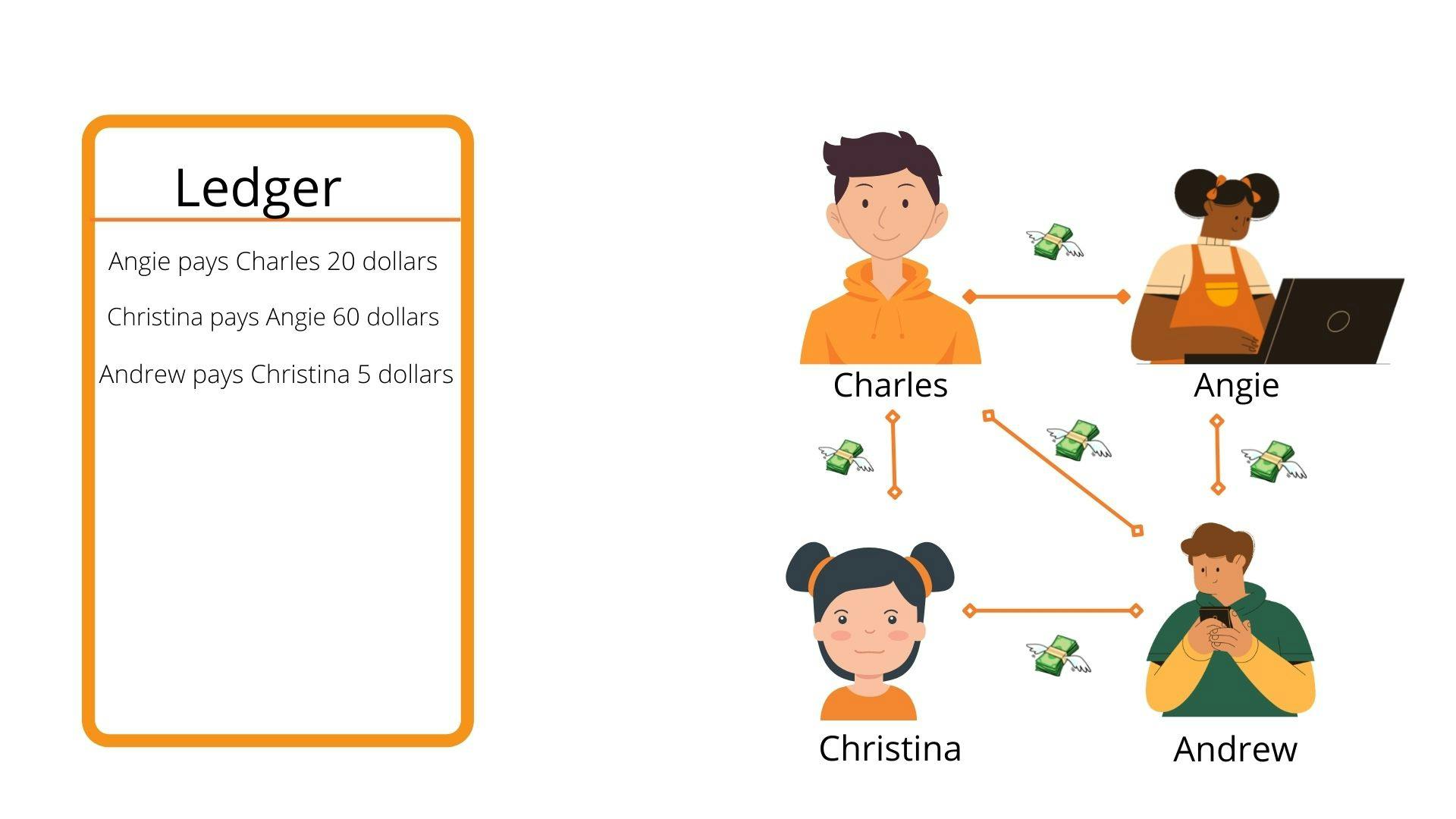 An example of a simple public ledger system for paying money.
An example of a simple public ledger system for paying money.
On this system, Angie created:
Anyone can add a line on the ledger.
Everyone receives or sends money to the people they owe at the end of the month.
This system seemed to work well with no complaints for the first few months because they were friends and had trust for each other. After a few months, Christina complained about how much she was asked to pay because she never recalled spending that much money. After many disputes, she insisted that there should be a better way of recording transactions on the ledger to make it more secure. Charles suggested that we sign on every transaction to prove that we have seen and approved like a contract. Andrew laughed that idea off, saying that someone can easily forge a signature on the ledger and that it is not secure enough. During the dispute, Angie, a computer science student, remembered a concept she was taught called Cryptographic Hash Functions. She interrupted the argument by saying, "we can use a digital signature by creating a program that maps our messages on the ledger to a secret key that we own. We can use a public key available to everyone to validate the entries."
A digital signature is an electronic signature that we can use to authenticate the message we write down. We must create a function that depends on the message and the private key(sk) to produce this signature.
Sign(Transaction, sk) = Signature
The private key(sk) is used to create a cryptographic hash function of the message and produces a fixed size output of enciphered text called the hash value, which no one can decipher unless you know the private key.
To verify that the transaction we wrote down in the program is valid, we would cross-check against the public key to check whether the transaction was true or false.
Verify(Transaction, Signature, pk) = True or False
In High-level terms, we can think of this verification system as when you were a child and your Guardian picked you up from school every day. Your Guardian acted as the secret key, and they were the only ones allowed to pick you up from school by signing you out.
An Example of what the cryptographic hash function would look like:
We have a Ledger where the transactions are secured by a digital signature using the SHA 256 algorithm, making it highly infeasible to find a valid signature if you do not know the secret key. Each transaction would also have a unique ID to avoid duplication of entries.
The protocols on the new system Angie created:
Anyone can add lines to the ledger.
Everyone receives or sends money to the people they owe at the end of the month.
Only signed transactions are valid and unsigned ones are invalid.
Each transaction also has a unique identifier or nonce to avoid duplication of Entries.
This system seemed to work fine until after the month Andrew relocated to a different school. They found out that he racked up 1000 dollars in debt at the end of the month, which caused an uproar and a lot of infighting. Suddenly no one could trust each other anymore with their money. The problem got Angie visibly upset, and she raised a new idea, "what if we all put in an initial amount, and no one would be allowed to spend more than they have on the ledger."
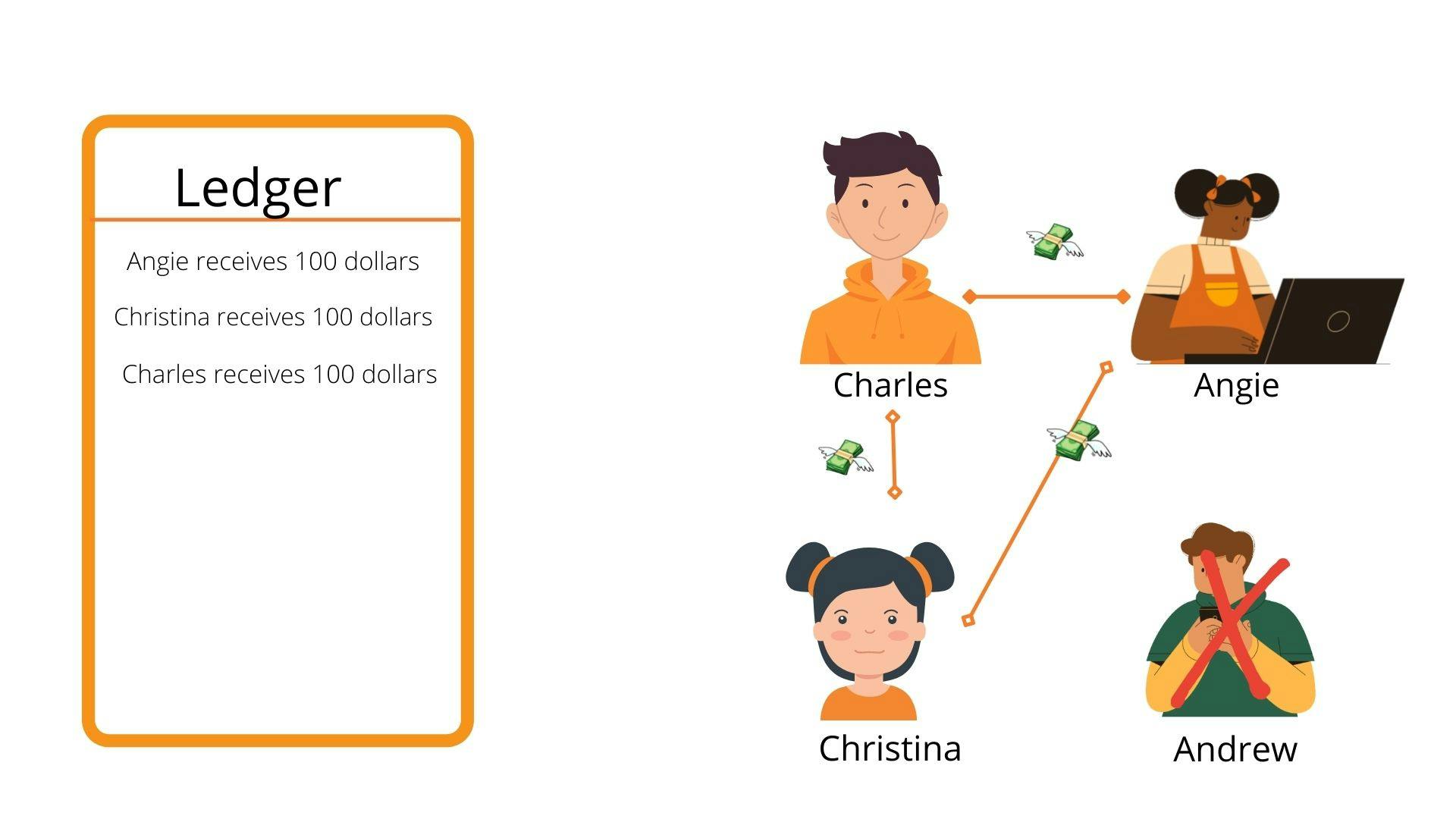 The new Ledger system, excluding Andrew, where everyone deposits 100 dollars and is not allowed to spend more than their deposit.
The new Ledger system, excluding Andrew, where everyone deposits 100 dollars and is not allowed to spend more than their deposit.
This new system Angie created seemed to work so well that other dorm houses started using her program, and soon the whole university started using the ledger as a means of exchange. Angie created her token called AngCoin, which they used for the exchange, so students traded money for Angcoin because it became the primary source of exchange in the university. After a while, there were many speculations about insider trading and artificial spikes in the token. They said she was only using it for her gain, which was not true. Still, she steered off all the criticisms. Eventually, she decided to open source her program and give everyone a copy of the ledger to monitor the transactions themselves to ensure nothing was fishy. So, each time a transaction occurs, the program would broadcast the transaction to everyone in the university to add it to their ledger.
The new protocols for this system that Angie created looked Like this:
Anyone can add lines to the ledger.
Everyone receives from or sends money to the people they owe in terms of tokens(Angcoins).
You can trade real currency for a signed transaction line on the ledger.
Only signed transactions are valid and unsigned ones are invalid.
Only signed transactions are added to the ledger.
Each transaction also has a unique identifier to avoid duplication of entries.
Each person on the block had a copy of the database, making it decentralised.
This new system bred distrust because anyone could broadcast a wrong transaction on the ledger. When people get incoherent blocks, they would have to manually check which transaction has been signed and which one has not, and with the scale of the system, this process was very cumbersome. So Angie devised a way to discourage people from putting a wrong transaction on a block by creating a proof of work algorithm that has to be solved for each block to be added to the chain, and every time the block creators(miners) solve the algorithm, the system would reward them with Angcoins that does not need to be signed by anyone.
The bitcoin proof of work consensus needs to have a minimum of 17 zeros in the hash function before the program can add it to the blockchain. It takes about 10 minutes for a new hash to be solved and for it to be added to the blockchain
People on the system would also pay these block creators to add their transactions to the block, but the transaction limit would be capped at 0.005 Angcoins per transaction.
A block can have more than 500 transactions going up to 8MB in size, and the average transaction fee is 80 satoshis.
It also means that the total number of Angcoins in the system increases with each new block added. So when using this transaction for payments, you would listen to coherent blocks that are being added on top of each other, so the key to this new protocol is that if you see two conflicting blockchains, you hear for the longest blockchain that you can trust, the longer the chain, the more you can trust it because that is the one with the most computation work. If they are of the same length, wait until you see an additional block that makes one of them longer with the most computational work. Each block also depends on the previous hash of the block added to it, so a change in one block affects all the blocks in the chain, causing an avalanche effect. This system makes it easier for people to act in good faith as it would be more expensive to act maliciously on the system.
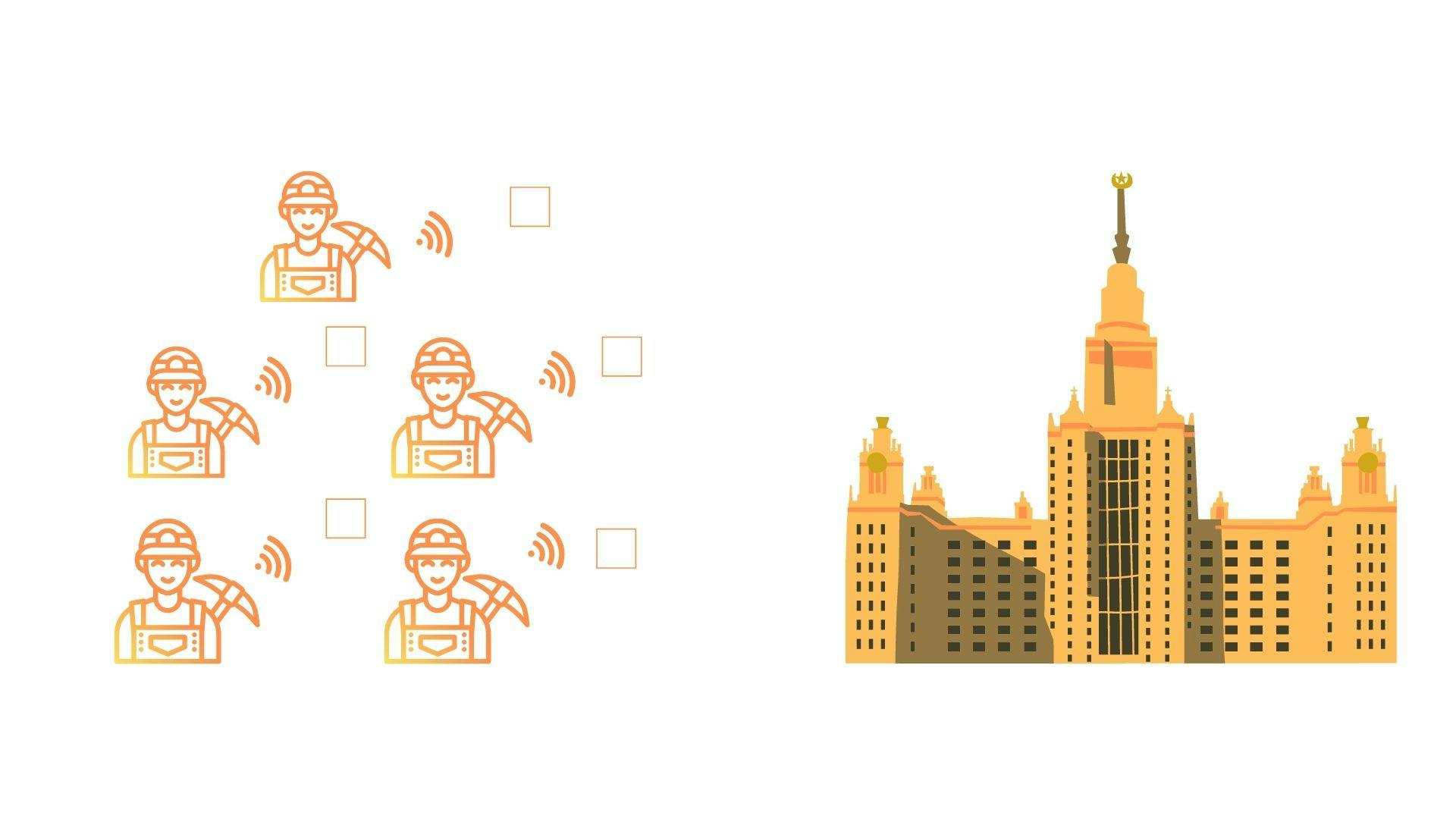 Block Creators(Miners) sending the blocks they have mined to the university for everyone to add to their ledger.
Block Creators(Miners) sending the blocks they have mined to the university for everyone to add to their ledger.
On the bitcoin protocol, miners are paid 6.25 bitcoin for each block they mine, and the amount they get paid reduces by half every four years making it so that they are only 21 million possible bitcoins that can be mined ever.
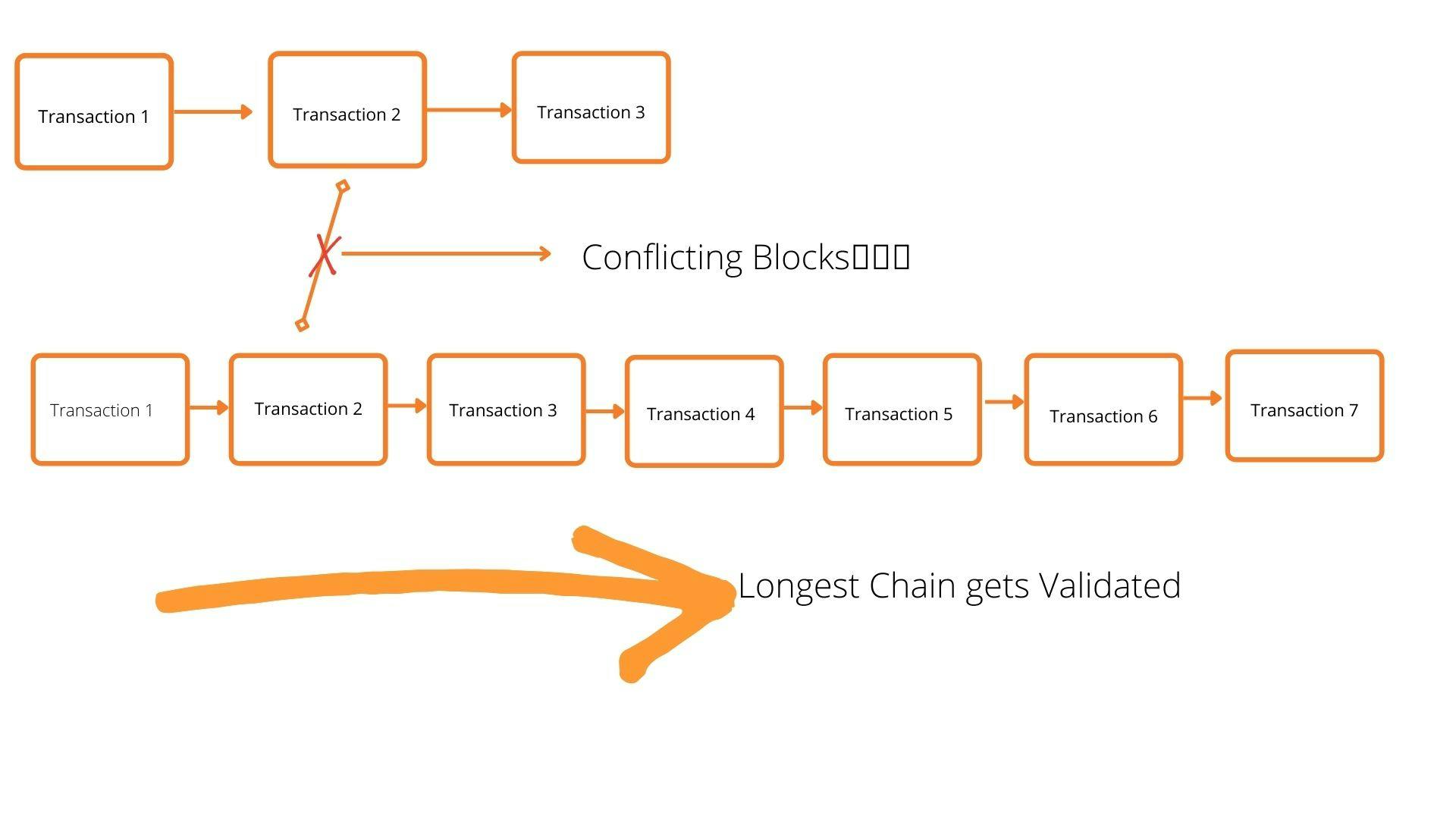 The longest chain in the blockchain is getting validated.
The longest chain in the blockchain is getting validated.
A simple implementation of the blockchain technology using python:
Output:
The nonce for the genesis block: 175
The nonce for the second block: 133
The nonce for the third block: 708
Hash for the genesis block:
003fa7db7fd704d200ccb8b8bba927fa107a015613ca46e9be44f449ba230876
Hash for the second block:
00d7e08a9db22ba7e5b739b3efc3e7f25d34df2147d0a9f8efd7f54b6845791a
Hash for the second block:
003cec13eb3e0243911adcef36221a796c3778623d4835376c51a4cf82e73850
This system leads to trust in decentralised computational work. This system still has a lot of problems, like a Sybil attack happening, which occurs when a centralised authority controls 24 per cent of the chain, which can allow them to do some malicious activities. If they own more than 50 per cent of the computational resources on the chain, they can deceive people into thinking the blocks being added are valid. Still, the threat of this attack is lowered when more people are on this system as it becomes very resource-intensive.
On the bitcoin system, it would take up to 80 billion dollars to control up to 50 per cent of the computational resources.
The protocols behind this new system are:
Anyone can add a transaction to a Block.
Only Transactions that have been signed are validated. The rest are invalidated.
You can buy tokens off-chain with physical currency to add a transaction to the block.
Each transaction also has a unique identifier to avoid duplication of Entries.
The block creators(miners) add the Valid transaction into a block.
You need to do proof of work before your block is added to a chain.
The block creators get a block reward based on the number of blocks they add to the blockchain.
Everyone has access to the blockchain or decentralised blockchain.
The longest chain is the blockchain that gets validated on the database, while the shortest chain gets invalidated by the users on the system.
Everyone receives or sends money to the people they owe based on their transaction history on the decentralised ledger in terms of tokens(Angcoins).
Bitcoin protocols were limited
On a high level, this concept is the basis for which bitcoin exists using the blockchain protocol. Satoshi Nakamoto created this protocol as a way for assets (Bitcoin) to be exchanged on a decentralised and trustless platform to create a global currency from a blockchain that is not created by a centralised government or controlled by a centralised banking system. The protocols were designed to be single-purpose tools created for one particular application. For the bitcoin protocol, it was digital assets, and for Namecoin, it was domain name registration. These protocols acted like a calculator and could not be used to do anything outside the scope of the protocol.
 A calculator to represent the blockchain protocols
A calculator to represent the blockchain protocols
This design presented a lot of bottlenecks for blockchain developers because it made it hard for developers to create decentralised applications or programs. They were some protocols that acted like a swiss army knife, but they were also limited by hindsight. Protocols were designed to do one thing, and one thing only, and developers needed to create a new protocol for each decentralised application they had in mind, which provided a massive roadblock for developers to create decentralised applications.
 Best I can do meme based on a swiss army knife protocol not being compatible with all computing use cases.
Best I can do meme based on a swiss army knife protocol not being compatible with all computing use cases.
While there are many criticisms of using decentralised applications, some are valid. From regulations issues, fraud, and the large-scale power consumption, this would have been the most significant bottleneck stopping decentralisation from reaching a wide-scale adoption because of the barrier of creating your protocol for every decentralised application.
 The amount of power consumption mining is set to use
The amount of power consumption mining is set to use
Why Ethereum was so important for the Blockchain Community
Ethereum was designed to be a general-purpose blockchain like an iOS, Android, or Windows Operating system. You can build applications on it instead of creating a whole new operating system to run an application. Ethereum could achieve this by having a Turing complete Virtual Machine where the Ethereum Virtual Machine(EVM) could store state in bytecode. Vitalik Buterin created the Ethereum Virtual Machine to handle any complex computation system that can happen on a finite state machine making it Turing complete- any machine that can do what a Turing machine can do is set to be Turing complete. The Turing machine, designed by Alan Turing, is a machine with a blank Tape of unlimited length - effectively a one-dimensional array that can grow infinitely at both ends - and allows it to read and write characters anywhere on the tape. A single tape serves as both storage and input: it can be prefilled with a string of characters to be treated as input. The machine can read those characters during execution and overwrite them if necessary. Having access to this tape allows us to solve new kinds of problems beyond simply accepting or rejecting strings. For example, we can design a Deterministic Turing Machine for incrementing a binary number on the tape.
They are six procedures for incrementing a binary number on a Turing machine:
Give the machine three states, 1, 2, and 3, with state 3 being the accept state.
Start the machine in state 1 with the tape head positioned over the rightmost digit of a binary number.
When in state one and a zero (or blank) is read, overwrite it with a one, move the head right, and go into state 2.
When in state one and a one is read, overwrite it with a zero and move the head left.
Move the head right when state two and a zero or one is read.
When in state two and a blank is read, move the head left and go into state 3.
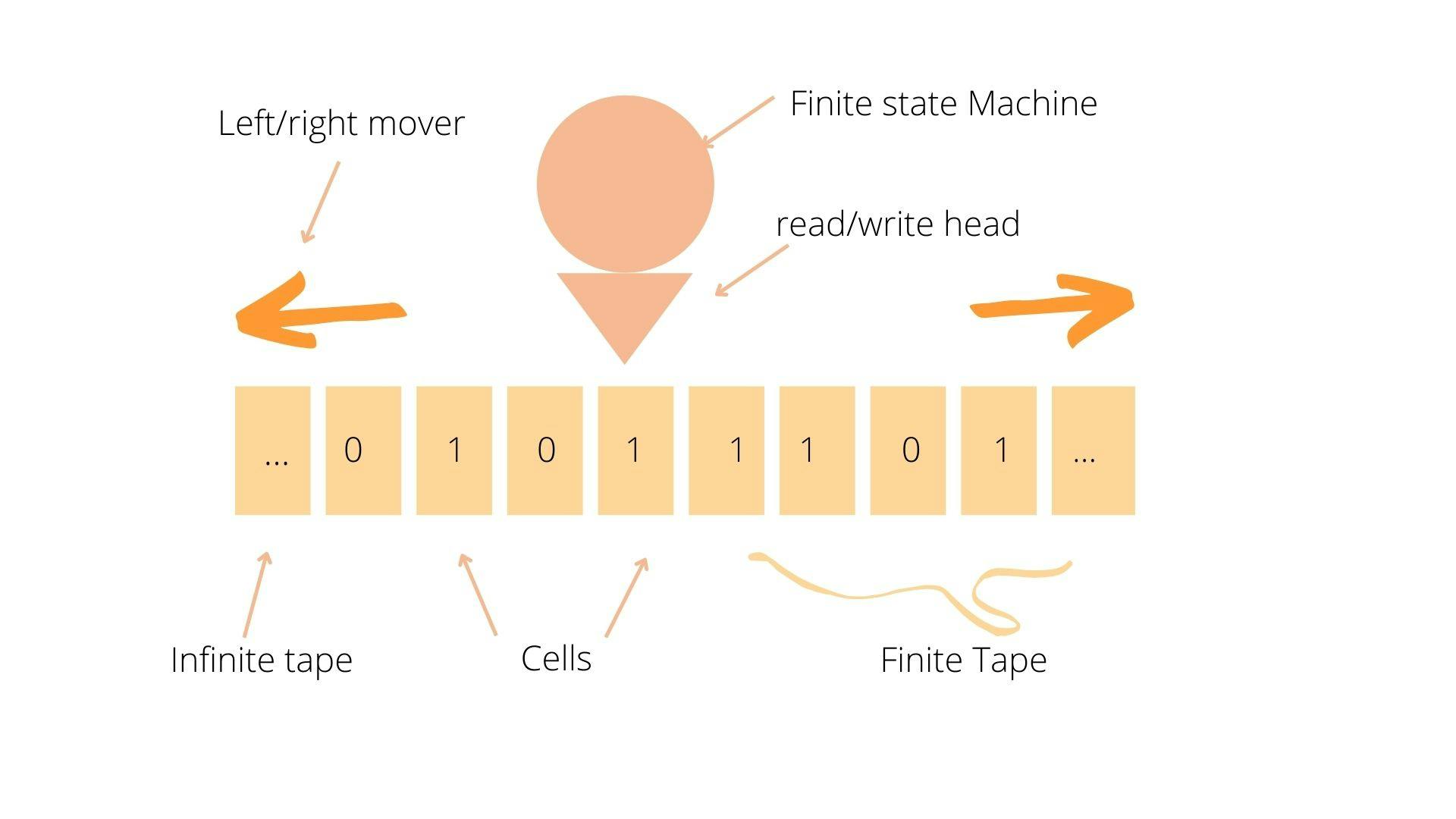 A Turing Machine incrementing a binary operation
A Turing Machine incrementing a binary operation
A finite state machine with access to an infinitely long tape is called a Turing Machine. All programming languages are Turing complete if the limitation of finite memory is ignored. A Turing Machine can solve any computational problem feasible if given enough time and memory. Ethereum's ability to execute a stored program in a state machine called the Ethereum Virtual Machine while reading and writing data to memory makes it a Turing-complete system and, therefore, a Universal Turing Machine. Ethereum can compute any algorithm computed by any Turing machine, given the limitations of finite memory. Ethereum is a deterministic but practically unbound state machine consisting of a globally accessible singleton state and a Virtual Machine that applies changes to the form using Smart Contracts.
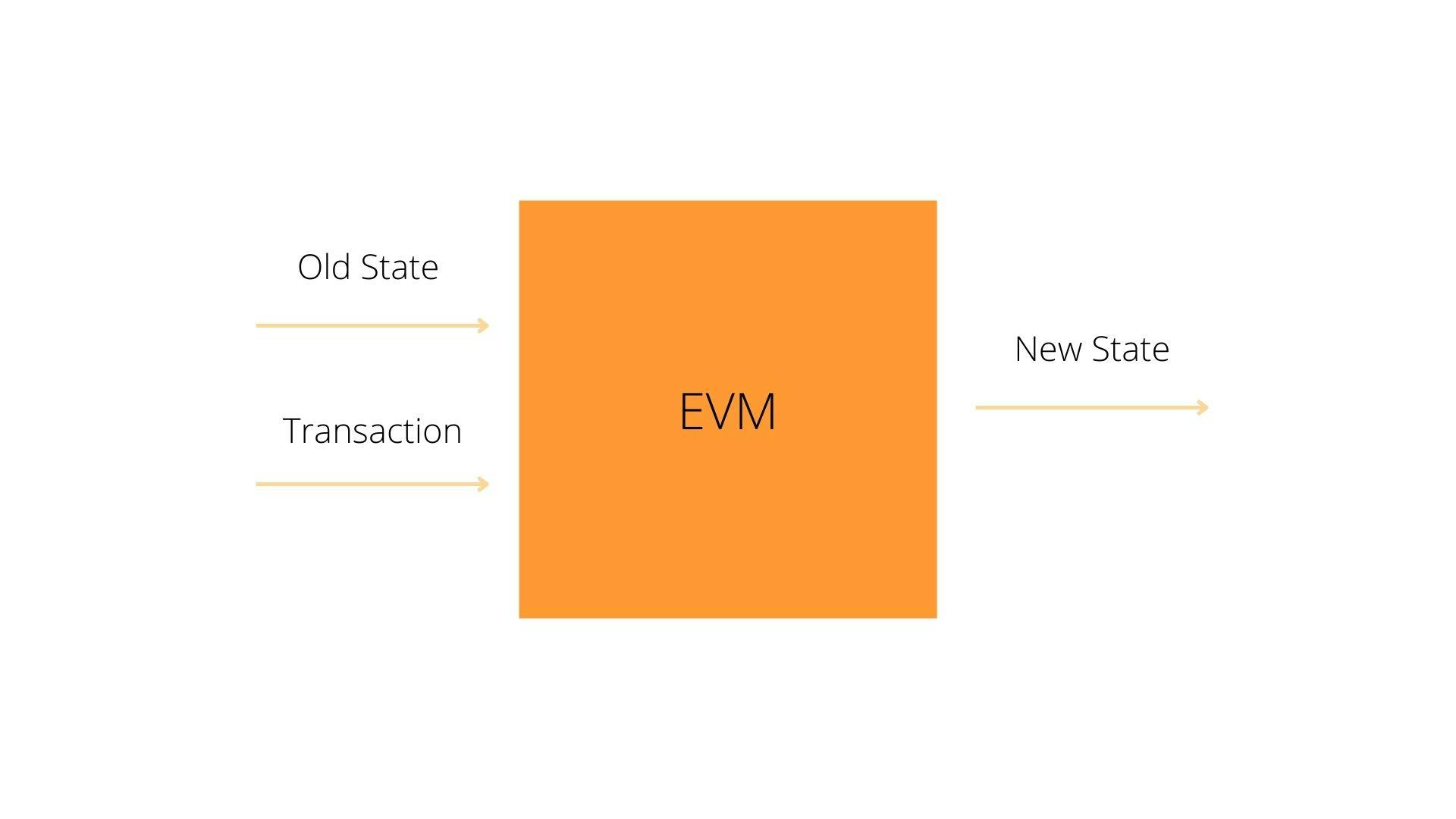
The Ethereum Virtual Machine enables developers to create powerful decentralised applications on the platform, such as social networking apps, messaging systems, Decentralized Autonomous Organizations (DAOs), etc., with very few limitations while still having the transparency that bitcoin offers and being more carbon-friendly with the introduction of proof of stake in Ethereum 2.0.
Turing completeness, however, does come with its drawbacks, such as the halting problem proves that you cannot predict whether a program will terminate anytime you simulate it on the machine. Other Turing machines, such as a printer, can be stopped from the source if it runs on an infinite loop, and in the case of a microwave oven, it can be controlled by exploding if it keeps running on an endless loop.

Unfortunately, a decentralised system does not have a "ctrl + C" when this issue arises -if it did, then it is not decentralised. Adding a smart contract that runs infinitely, whether accidentally or intentionally, would lead to a form of DOS attack. The Denial-of-Service(DoS) attack is created to shut down a machine or network, making it inaccessible to its intended users. For Example, A DoS attack can happen in a small shop where many people come into it on a hot day and pretend to be shopping to escape the heat because the shop is air-conditioned. This situation kept happening until the shop was at capacity. Still, no one was buying anything, and some people were stealing, and it became hard to keep track of it because of how many people were around, and you would run at a loss at the end of the day. Denial Of Service Attacks waste many resources that other nodes could use to process smart contracts. The solution Ethereum had to this was creating gas fees. As the EVM executes a smart contract, it carefully accounts for every instruction (computation, data access, etc.). Each instruction has a predetermined cost in units of gas. When a transaction triggers the execution of a smart contract, it must include an amount of gas that sets the upper limit of what can be consumed running the smart contract. The EVM will terminate execution if the amount of gas consumed by computation exceeds the gas available in the transaction. Gas is the mechanism Ethereum uses to allow Turing-complete computation while limiting the resources that any program can consume. So Ethereum is more of a quasi Turing Machine using the benefits of its computational power while accounting for the Halting problem with gas fees which we can buy with ether.
Components of the Ethereum Blockchain:
A peer to peer( P2P) network connecting participants and propagating transactions and blocks of verified transactions, based on a standardised protocol.
Messages, in the form of transactions, represent state transitions.
A set of consensus rules governing what constitutes a transaction and what makes for a valid state transition.
A state machine that processes transactions according to the consensus rules.
A cryptographically secured blockchain acts as a record of all the verified and accepted state transitions.
A consensus algorithm that decentralises control over the blockchain by forcing participants to cooperate to enforce the consensus rate.
A theoretically sound incentivisation scheme(Proof of Stake, gas fees) to secure the state machine in an open environment economically.
One or more open-source software implementations of the above ("Clients").
Ethereum answers the question: "what if we could track any arbitrary state and program the state machine to create a worldwide computer under a consensus protocol." - Dr Gavin Woods, Mastering Ethereum
 Vitalik Buterin, Co-Founder and CEO of Ethereum, speaking at Devcon.
Vitalik Buterin, Co-Founder and CEO of Ethereum, speaking at Devcon.
Problems with Ethereum being Turing Complete
Ethereum, however, does come with a lot of drawbacks from its seemingly unsafe design of the Ethereum Virtual Environment and lack of modern Virtual Machine features such as a dispatch and abstraction must be handled entirely by the user-facing language, which leaves language designers, such as the authors of Solidity, with a tough job, and a bevy of opportunities to make critical mistakes. The bytecode model also makes it challenging to read on-chain and must be decompiled to be debugged or validated. Any language built on top of the EVM, in contrast, will produce bytecode that will be illegible and unverifiable by humans and thus will only ever yield an incomplete understanding of the functionality of the programs written in that language. This design decision makes Ethereum prone to a lot of attack vectors.
Bitcoin fixes this...
Bitcoin provides a safe, simple, and effectively readable bytecode language intended to guarantee the consistency and correctness of programs run on the blockchain. It offers a minimal instruction set and uses bytecode primarily to keep payloads small. It was intentionally made Turing incomplete by the creator(s), making it more accessible and efficient to work with the protocol.
Conclusion
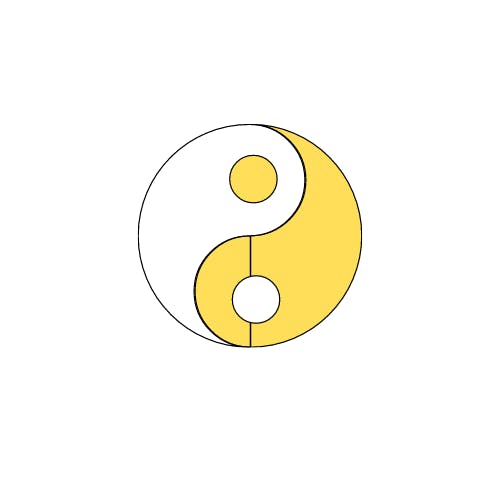 The Yin and Yang Symbol where the white represents the Bitcoin White Paper and The Yellow represents the Ethereum Yellow Paper.
The Yin and Yang Symbol where the white represents the Bitcoin White Paper and The Yellow represents the Ethereum Yellow Paper.
The Bitcoin and Ethereum protocols are equally important for the blockchain community and need each other to reach full-scale adoption. While bitcoin is laser-focused on being a store of value, Ethereum can work towards being a better, faster, and more efficient general-purpose computer with future iterations.
References for further reading
- The bitcoin white paper by Satoshi Nakamoto
- The Ethereum documentation
- Mastering Ethereum by Dr Gavin Woods and Andreas Antonopoulous
- Understanding Computation by Tom Stuart
- The Halting Problem
- Cryptographic Hash Functions and Digital Signatures
- DEVCON1: Understanding the Ethereum Blockchain Protocol - Vitalik Buterin
